Secure Logins with Browser Keys
It’s hard to write about internet security while keeping things simple. Those of us who know it well forget how difficult it can be to first get one’s head around the fundamental concepts. Take for example asymmetric cryptography (a.k.a., public key cryptography), which is the foundational concept for secure internet browsing and keeping private information safe from prying eyes.
After a couple of attempts to write an easy to understand explanation of using public key cryptography to authenticate oneself (i.e., login securely) to a website, I was frustrated at my inability to break it down into simple terms. I then asked AI to explain it to me like I was 7 years old:
Imagine you’re trying to get into a super cool, secret playground. To get in, you need to prove that you’re really you. Here’s how you can do it using a special pair of keys:
Your Secret Key (Private Key): This is like a special password that only you know. You keep it safe and don’t tell anyone.
Your Public Key: This is like a special name tag that you can share with others. It’s connected to your secret key, but it doesn’t reveal what your secret key is.
When you want to get into the playground, you use your secret key to sign a special ticket. This ticket says, “I’m really me!” The playground then checks this ticket against your public key to make sure it was really signed by you.
Here’s how it works:
You use your secret key to create a special signature on the ticket.
You send the ticket to the playground.
The playground uses your public key to verify the signature. If it matches, they know that only you could have signed it, because only your secret key can create a signature that matches your public key.
This way, you prove that you’re really you without sharing your secret key with anyone. The playground trusts that you’re who you say you are, and they let you in! This is similar to how asymmetric cryptography is used for authentication in real-life systems.
It’s a good explanation that introduces the public/private key pair and describes how the public key is used to confirm ownership of the private key.
The “something you have” (e.g., a private key) form of security is more secure than the “something you know” form (e.g., username/password) because it is easier to steal a password than to steal a private key from secure storage, whether that storage is a secure hardware device or just a well-implemented storage system in software. This is why technologies like fingerprint readers and facial recognition are now widely adopted as authentication mechanisms. Embedded in those technologies is a public/private key pair that is used to sign “tickets” to get you into the “playground” once the fingerprint or face is recognized and confirmed valid by the secure device that processes it.
Public key cryptography in web browsers (what we call “browser keys”) are another way to leverage a secure environment (the web browser’s secure storage environment) to create a key pair and sign “tickets”. It does not require specialized hardware (e.g., expensive laptops and smartphones!). You just need to be running a current version of any of the major browsers: Chrome (and other Chromium-based browsers like Edge, Brave, Vivaldi, etc.), Safari and Firefox.
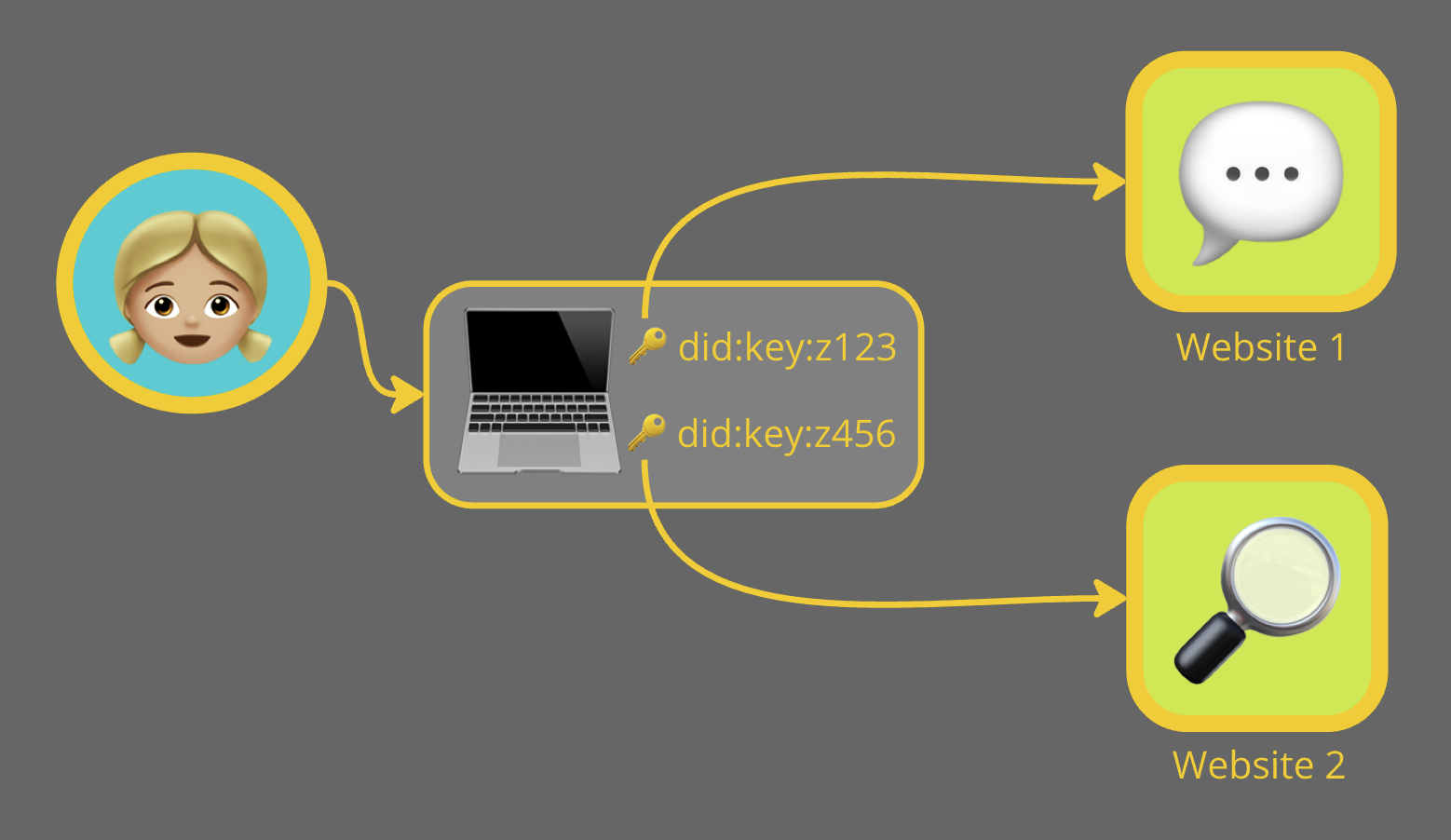
In the image above, Alice shares a unique public/private key pair with each website she visits. The browser automatically handles the key pairs for her so she does not have to worry about which key pair to use with which website.
The user experience with browser keys is excellent. Registration simply involves entering a username to identify yourself when using the website. The keypair is generated automatically when you first visit the site, and the public key is collected by the website from your browser when you set your username.
Logging in is even simpler. Just open the website and you are immediately logged in!
We will write another blog post showing how it works when we have finished. For now it is work in progress here:
https://github.com/ic3software/did-auth